
An Industrial Control System (ICS) refers to a system that combines both Operational Technology (OT) and Information Technology (IT) to supervise and regulate processes in industries. The key distinction, between OT and IT lies in their respective focuses; OT concentrates on control of the processes to ensure availability and safety while IT centers on data management and security. Securing an ICS can be challenging due, to the differing technological constraints of OT systems compared to IT systems. As technology progresses the integration of IT and OT is increasing, which also raises cybersecurity concerns.
The IT and OT are different in the way they operate, the technology they use and the way they are managed. These differences create unique challenges and limitations for the security of ICS systems. This article will explain these challenges by giving examples of how cybersecurity procedures, technologies and investments are different from IT environments.
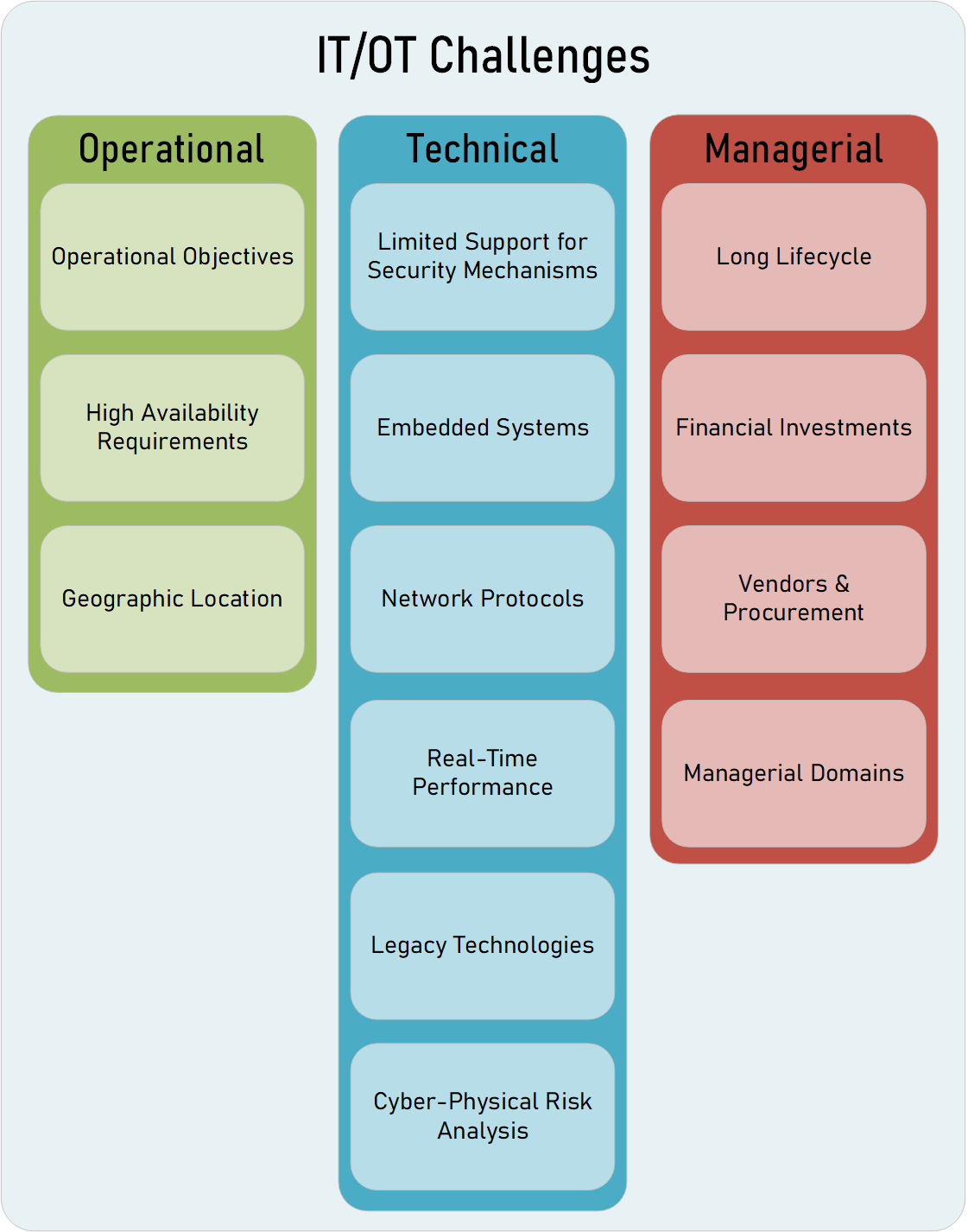
Factors Influencing Differences between Operations Technology and Information Technology
Operational
The main goal of an ICS is to control and monitor physical processes like power grids, gas pipelines, and manufacturing systems using a combination of sensors, actuators, controllers, and human operators. This creates unique requirements that are different from traditional IT systems. In IT systems, the main focus is on managing and controlling data, so security mainly focuses on maintaining confidentiality, integrity and availability of that data. In contrast, ICS security must also focus on ensuring the safety, environmental compliance, interdependencies and profitability of the physical process being controlled. Additionally, the ICS must operate in real-time and be highly available, and there are also regulatory and environmental considerations to take into account. This section will go into more detail on these unique operational challenges.
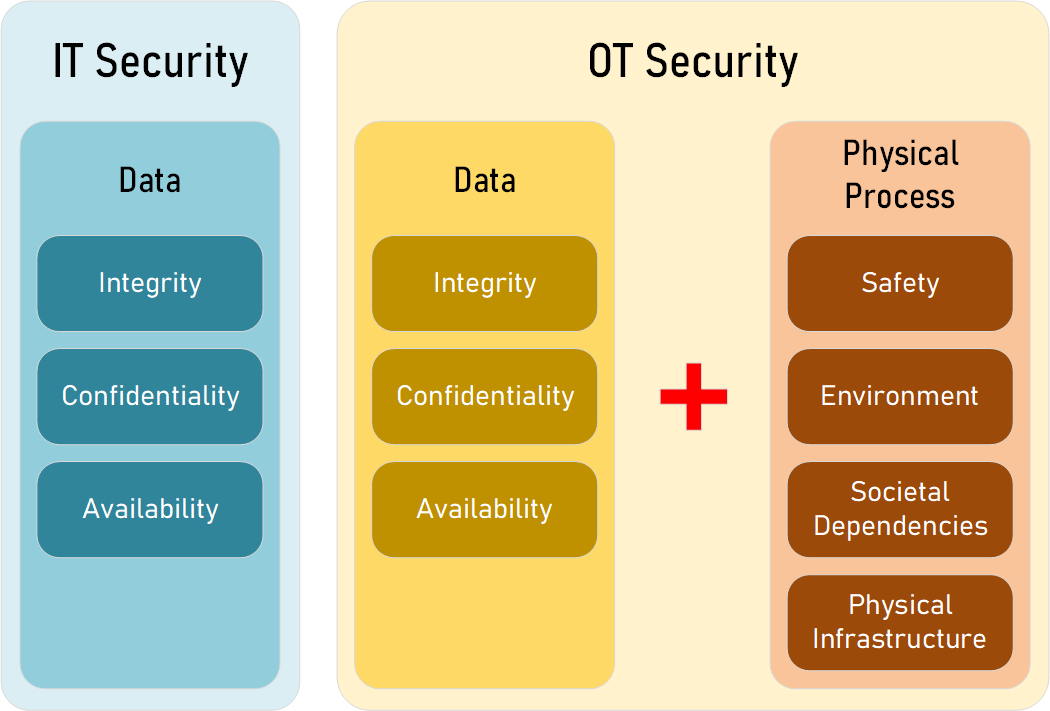
Operational requirements of OT versus IT
Operational Objectives
An ICS has multiple goals that need to be balanced while it is operating. These goals include minimizing safety or environmental risks, managing the system’s impact on society, protecting physical assets, and maintaining profitability. Cybersecurity is important to support these goals, but it is not the main focus. The organization must balance the importance of cybersecurity with other operational challenges.
Safety
An ICS can cause harm to people and the community if it doesn’t work properly. Safety hazards can include things like explosions, electric shocks, radiation, and chemical releases. Because of these risks, safety is a top priority for ICS operators. They use special systems to monitor safety and have procedures and policies in place to prioritize safety. In the past, people have been killed because of ICS failures, for example, the ammonium nitrate explosion at the West Fertilizer Company in Texas, United States in 2013, which killed 15 people and injured more than 160 others, the cause of the incident was linked to a failure in the ICS system that was responsible for monitoring and controlling the ammonium nitrate storage and handling.
Environmental
An ICS failure can also harm the environment by releasing dangerous chemicals, radiation or other materials. This can damage plants, wildlife, air and water quality. An example of this is the incident that occurred at the Maroochy Water Services sewage treatment plant in Australia in 2000, where a person was able to remotely access the plant’s wireless networks on multiple occasions and used that access to dump sewage into nearby rivers. This resulted in hundreds of thousands of gallons of sewage being released into the local waterways, causing environmental damage and raising concerns about the potential risks of cyber-attacks on ICS systems.
Societal Dependencies
The malfunction of ICS can also have an impact, on interconnected systems and infrastructures known as interdependencies. For instance critical infrastructures such as the power grid, transportation systems and communication networks can be affected. These infrastructures play a role in the functioning of society. A notable incident illustrating this is the power outage that occurred in the Northeastern United States in 2003. It was caused by a failure in a SCADA system operated by the Midcontinent Independent Transmission System Operators (MISO). This failure resulted in a power outage affecting 50 million people and causing an economic loss estimated between $4 to $10 billion. The SCADA system failure was triggered by a software bug that hindered operators from obtaining an overview of the grids condition ultimately leading to a cascading failure, within the power grid. This highlights the importance of the ICS systems in maintaining the integrity of critical infrastructures and the potential consequences of an ICS failure on society.
Physical Infrastructure
ICS failures can also damage expensive physical components of the system such as generators, motors, pipelines, and storage tanks. These components are costly to replace or repair and can cause long system outages and high expenses. In some cases, cyber-attacks on ICSs have resulted in physical damage to the system. The Stuxnet malware is an example of physical infrastructure being damaged by a cyber-attack where it infected PLCs and caused damage to uranium enrichment centrifuges. An experiment conducted by Idaho National Laboratory (INL) showed that an attack on the electric grid could also damage generators where a protection relay was hacked and used to repeatedly trip and open a circuit breaker, which caused the destruction of the generator.
High Availability Requirements
ICS often need to work non-stop, which makes it hard to add security measures. Examples of these types of systems include power grids, water and gas systems, and manufacturing systems. These systems usually need to be working 99.99-99.999% of the time, which means they can only be shut down for a short amount of time each year. This downtime must also include unexpected problems and maintenance. This means that all maintenance must be done during one scheduled shutdown each year or every six months.
This high availability requirement makes it difficult to add security measures. For example, to add a security patch or update, the system needs to be rebooted, which can cause a loss of availability. Installing a patch can reduce the risk of a cyber-attack, but it can also increase other risks caused by the shutdown. The operator must weigh the risks carefully. Often, the ICS must wait until the scheduled shutdown to install the patch.
Additionally, Security assessments, like penetration testing and vulnerability assessments, are also difficult to do. These tests can slow down or even crash the system. There are examples of systems being damaged during security assessments. For example, a failed SCADA server locked up an oil pipeline, and a system scan destroyed a batch of integrated circuits in a chip factory.
Finally, Security mechanisms, like authentication and firewalls, often “fail-closed” which means they block access to protect the system. However, this can also impact the ICS if they block authorized access. For example, a firewall misconfiguration could block important messages or an operator entering the wrong password could be unable to perform a critical task.
Because security measures can impact the correct operation of the ICS, there is often a conflict between safety and security.
Geographic Location
ICS systems often have to operate across different locations, for example electric power grids can span over many miles, and oil pipelines can stretch across vast distances. This can make it hard to protect the system from physical tampering. If someone can access a remote device, they can change how it works, fake data from the device, or get access to system information. If an attacker can physically access the system, they can get important data like passwords and encryption keys, which can give them more access to other parts of the ICS. Also, securing a distributed system can be difficult because it requires remote management and access. This means that operators and engineers may not always be able to physically access the system and must use remote administration interfaces to control it. However, these same interfaces can also be used by attackers to gain unauthorized access to the system.
Technical
ICS systems have specific technical needs for their software and communication platforms. These include using different communication methods, needing real-time performance, using devices with limited resources, using specialized equipment from certain manufacturers, and combining digital, analog, and mechanical controls. These technical requirements make securing ICS systems different from securing regular IT systems.
Limited Support for Security Mechanisms
OT systems often don’t have enough security features to protect the ICS. It’s important to understand the technical abilities of each system to make a plan to protect it. NIST 800-82 talks about the security controls needed to protect ICS and the challenges of using these controls with the lack of security features in many OT systems.
Embedded Systems
Embedded systems in ICS environments have limited resources and can’t support many security features. They often can’t run software like intrusion detection or anti-virus because it takes too much processing power. They also need to perform real-time tasks, leaving little time for security. This can also increase power consumption and reduce the lifespan of battery-powered devices.
Network Protocols
ICS uses a variety of network protocols, including ones used in traditional IT and specific ones for OT. Some of these protocols are different between IT and OT, and they have different characteristics and different types of security. Some of the main differences include:
- Security capabilities: IT and OT have different security features. IT protocols have newer versions that have added security, such as HTTPS, DNSSEC, and IPv6. OT protocols prioritize maintaining reliable and error-free communication but do not provide additional security against cyber threats. Some OT protocols have started adding security features, but they are not as common as in IT.
- Limited support of security devices: Security devices like firewalls and IDS may not work well with the protocols used in OT systems. These devices may not have enough support for the unique parameters of the OT protocols, making it hard to create rules for them. This means that the security rules for these devices also have to be specifically designed for the protocols used in OT systems.
Real-Time Performance
ICS systems have to work in real-time to manage physical processes. This means that the communication between systems has to be very fast and not vary much. OT systems can have difficulty incorporating security features like encryption and authentication as it can be time-consuming and resource intensive. Many ICS systems in power systems have concerns about adding these security measures because they take too long. Standards like IEC 61850 and the American Gas Association have identified these challenges and looked into ways to make it work. Some research has shown that certain security measures take too long and can’t be used in ICS systems that need to work in real-time. This is because ICS systems need to communicate and respond quickly, but the security measures take too long to be added to the communication.
Outdated Technologies
ICS systems often use old and rare technologies that make it hard to add security measures. These old systems typically don’t have enough security to protect against modern threats, such as encryption and authentication of messages sent across networks. These systems also often lack user authentication, access control, and auditing capabilities. They also have not undergone rigorous security testing during their design to verify they don’t have security vulnerabilities or backdoors. To protect these old systems, ICS needs to deploy additional technologies, such as VPNs and firewalls that can encapsulate the old devices and implement required security functions. These rare technologies also make it hard to find skilled professionals to administer the system and to perform necessary security assessments.
Cyber-Physical Risk Analysis
Assessing the potential cyber-attacks on physical systems can be a challenging task due to the complexity of the control and monitoring systems that combines both IT and OT environments. These systems include digital, mechanical, electromagnetic, and analog elements that may not be directly susceptible to cyber-attacks unless they can be controlled by other digital systems. As a result, it can be difficult to comprehend how an attacker could manipulate the system. This complexity makes it hard to evaluate the risks of a cyber-attack accurately, and the additional protections in place may result in underestimating the risk.
Managerial
Managing OT systems is different from managing IT systems. One key difference is that the cost of investing in the infrastructure for these systems is often higher and these systems must be in operation for many years to retrieve the costs. Additionally, the revenue streams for these systems may be more limited which can affect the cybersecurity budget of the organization. This section will discuss these issues and their impact on security.
Long Lifecycle
ICS systems are often more expensive to set up and maintain, and they need to be in operation for a long time to recoup the investment. For example, power system relays are typically used for more than 20 years, while IT systems have shorter lifetimes of 3-5 years. This long lifecycle poses cybersecurity challenges, specifically in addressing new threats and relying on outdated systems. IT systems have shorter lifetimes making them more adaptable to new threats, while ICS systems often struggle to keep up. For example, older encryption methods and protocols are no longer considered secure. Additionally, many old software platforms like Windows XP are no longer supported and vulnerabilities in these systems will not be patched.
Financial Investments
ICS systems, such as those used in power plants, water treatment facilities, and oil and gas refineries, often have a fixed revenue structure, which limits their budget for cybersecurity. This means that the revenues generated by these systems are usually tied to their operating costs, capital investments and regulatory compliances. For instance, a power plant may have a fixed amount of money allocated for cybersecurity measures, but if a new cyber threat emerges, the power plant may not have the funds to invest in new security measures to protect against the threat. The lack of flexibility in the budget allocation can make these systems more vulnerable to cyber-attacks as they may not be able to respond quickly to new threats.
A water treatment facility may have to invest in cybersecurity measures to protect the water supply from cyber threats, but the budget may not be sufficient to cover the cost of these measures. This can create a gap between when cybersecurity investments are needed and when the facility can afford to make the investment. In addition, the lack of budget can make it hard for the facility to keep their systems updated with the latest security patches, software and technologies.
In the oil and gas industry, refineries also face similar challenges as they have a fixed revenue structure, which may not allow them to invest in cybersecurity measures beyond the allocated budget. For example, a refinery may not be able to invest in advanced security technologies like AI-based intrusion detection systems, and this can make them more susceptible to cyber-attacks.
Overall, ICS systems that have a fixed revenue structure may face challenges in obtaining enough funding for cybersecurity measures due to budget constraints, which can make them more vulnerable to cyber threats. This is why it’s important for organizations to plan and budget for cybersecurity measures, and to work with regulatory bodies to ensure that the necessary funding is provided to protect these systems.
Vendors & Procurement
ICS systems have different product vendors and procurement processes than IT systems, which can affect how security is managed throughout their lifetime. For example, IT vendors usually have clear policies for handling vulnerabilities and releasing patches, but ICS vendors often do not. Also, IT systems have tools to help manage and install patches, but ICS systems may not. Vulnerabilities in ICS systems often go unpatched, and if a patch is available, it may not be installed because it could affect system availability. Updating ICS systems requires additional testing to ensure reliability and compatibility with other OT software platforms.
ICS systems may not have a test environment to validate patches before applying them to production systems. Additionally, ICS systems often contract a third-party company to deploy and configure their systems, which means the ICS operator may not have deep technical knowledge about the communication and control technologies. This poses security challenges throughout the system’s lifecycle, such as being unable to effectively monitor the system for attack or intrusions, limited ability to plan for and recover from security incidents, and difficulty implementing security patches and updates. The ICS systems may rely on the third-party company to test and install patches, which can increase the system’s vulnerability period.
Managerial Domains
ICS systems also face cultural challenges in their management and administration. These systems have to manage both IT and OT technologies, which can create conflicts over who is responsible for managing different systems and software. One approach is for each domain to manage the systems that fall within their area of expertise. IT staff would manage IT technologies and vendors, while OT staff would manage OT technologies and vendors. However, this approach could cause problems if IT staff negatively impact the operation of the ICS by performing incorrect configurations or adding problematic patches. Another approach would be for IT staff to only support office automation systems and servers that don’t store or manage operational ICS data, while OT staff manage all SCADA and control systems. This approach could improve support for ICS operations, but it could also increase the system’s vulnerability since OT staff may not have in-depth knowledge of IT technologies. Additionally, it can be unclear where a system falls in terms of categorization as OT or IT. There’s a growing trend towards convergence of OT and IT systems in modern ICS, which further blurs the differences between the IT and OT domains by clouding administrative and managerial boundaries over the components of the ICS.
